Protecting Your SMB from Cyber Security Threats
Cyber Security
How to Protect Your Business Before It’s Too Late
As technology advances, small and medium-sized businesses (SMBs) need to be increasingly aware of the importance of cybersecurity. Cyberattacks target SMBs frequently, and the repercussions of a data breach can be devastating.

Typical issues handled within Level 2 and Level 3 include:
We hope you find this information helpful. Great Lakes Computer always recommends consulting with an expert to create or update your cyber security guidelines. Contact us with questions or to schedule a complimentary consultation.
Part I: Protect Your Business – Cyber Security Guide for SMBs
Part II: Email Security and Phishing
Part IV: Protecting Your Network
- Data Security: Can Hackers Take Control of Your Products & Equipment?
- How To Defend Your Network Security from 5 Wi-Fi Attacks
- 15 Must-Dos to Protect Your Business from a Cyber Attack
- Cyber Attack Check List
- Establishing Effective Company Cybersecurity Policies
- Endpoint Protection Platform: Edge to Edge Enterprise Security Platform
- SOC-as-a-Service: What You Need to Know
Part V: Training Your Team for Breach
Part VI: Backup and Disaster Recovery – Protecting your network
- Data Backup and Recovery Best Practices for SMBs
- Top 7 Disaster Recovery Questions & Answers
- Nothing is More Important Than Data Backup
- 5 Simple Data Backup Tips You Can Use Today
- Data Security MUST Include Regular Backup
- The Need for Online Backup: A Business Analysis
- Data Backup Government Regulations
- The Blue Screen of Death! A Good Lesson in Data Backup.
- Affordable & Effective Data Backup Options for SMBs
- 5 Data Backup Myths to Ignore
- Disaster Protection: Why Your Business Needs BCDR Now


Part IV: Protecting Your Network
- Data Security: Can Hackers Take Control of Your Products & Equipment?
- How To Defend Your Network Security from 5 Wi-Fi Attacks
- 15 Must-Dos to Protect Your Business from a Cyber Attack
- Cyber Attack Check List
- Establishing Effective Company Cybersecurity Policies
- Endpoint Protection Platform: Edge to Edge Enterprise Security Platform
- SOC-as-a-Service: What You Need to Know
Part V: Training Your Team for Breach
Part VI: Backup and Disaster Recovery – Protecting your network
- Data Backup and Recovery Best Practices for SMBs
- Top 7 Disaster Recovery Questions & Answers
- Nothing is More Important Than Data Backup
- 5 Simple Data Backup Tips You Can Use Today
- Data Security MUST Include Regular Backup
- The Need for Online Backup: A Business Analysis
- Data Backup Government Regulations
- The Blue Screen of Death! A Good Lesson in Data Backup.
- Affordable & Effective Data Backup Options for SMBs
- 5 Data Backup Myths to Ignore
- Disaster Protection: Why Your Business Needs BCDR Now
Content

Part I: Protect Your Business – Cyber Security Guide for SMBs
Small and medium-sized businesses are at risk of data loss and theft due to limited resources and the value of their assets, making extra security measures an essential factor for protecting data.
- strong internet security
- thorough security policies
- updated software
- backup measures
- physical security
Due to limited resources and higher costs per user, small businesses are at a greater risk for cyber-attacks and have a more difficult time finding experienced security personnel. By moving security to the cloud, small businesses can reduce the need for in-house personnel and lower costs, improving their protection against cyber threats.
Building a Disaster Recovery Budget
Small businesses must account for natural and man-made disasters when planning their disaster recovery plan. The budget should prioritize protecting data by having on-site and off-site backups, redundant firewalls and anti-virus software, and possibly using cloud storage or paying for a hot site.
- What is IT outsourcing?
- How do you know when the time is right to consider it?
- What IT services can be outsourced?
- What criteria should you use to choose a managed provider once you’ve decided to outsource?
- Ransomware-as-a-Service (RaaS)
- Phishing-as-a-Service (PaaS)
- Hacking-as-a-Service (HaaS)
- Crimeware-as-a-Service (CraaS)
Part II: Email Security
- Stolen login credentials
- Spyware and Trojan installation
- Payment fraud
- Ransomware installation


Part II: Email Security
- Stolen login credentials
- Spyware and Trojan installation
- Payment fraud
- Ransomware installation
- Dishonest information requests
- False link emails
- Spoofed website emails
- Executive fraud

Part IV: Protecting Your Network
- Lost or stolen device
- User-to-user snooping
- Sessions hijacking accounts
- Rogue access points
- Risk Assessment
- Written Security Policy
- Security Awareness
- Passwords
- Multifactor Authentication
- Advanced Endpoint Protection
- Web Content Filtering
- Encryption
- Firewall
- Backup
- Updates
- Access Control
- Penetration Testing
- Incident Response
- Cyber Insurance
- Create Strong Password Practices
- Two-Factor Authentication (2FA)
- Device Usage and Network Access
- Secure Email and Messaging
- Periodically Review Policies and Security Standards
-
 Mitigation
Mitigation -
 Immunization
Immunization -
 Remediation
Remediation -
 Forensics
Forensics
- Access to a team of security experts
- Centralized visibility with actionable outcomes
- Never deal with annoying false alarms
- A simplified and predictable pricing model
Part V: Training Your Team for Breach


Part V: Training Your Team for Breach
- Connect to a Secure Network
- Enable and Configure a Firewall
- Install and Use Antivirus and Antispyware Software
- Remove Unnecessary Software
- Modify Unnecessary Default Features
- Operate Under the Principle of Least Privilege
- Secure Your Web Browser
- Apply Software Updates and Enable Future Automatic Updates
- Use Good Security Practices
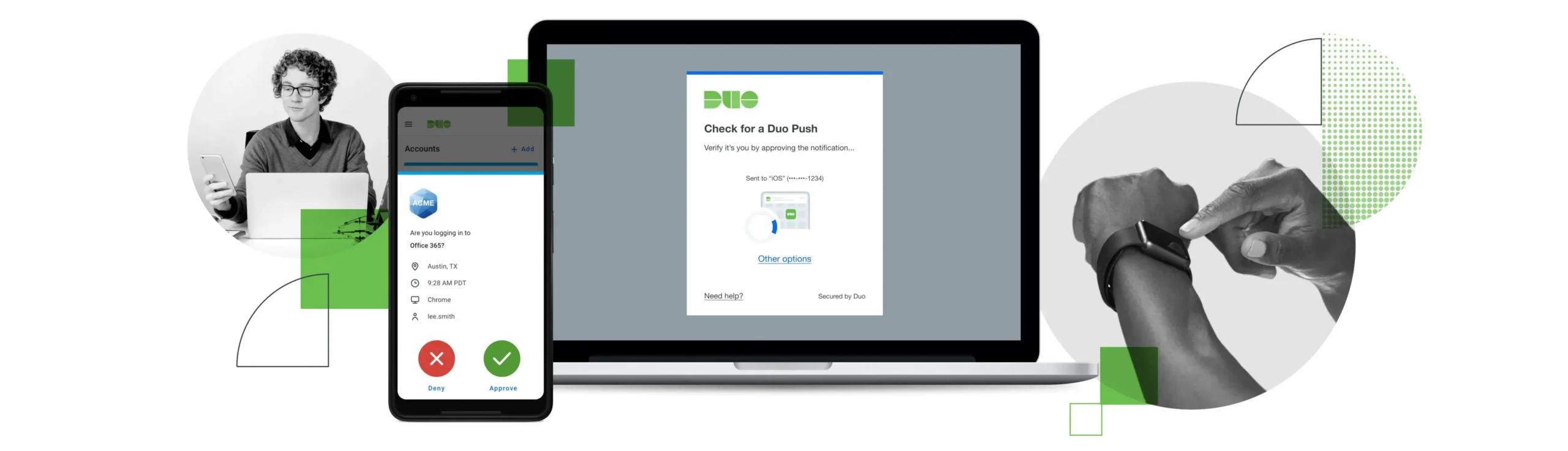
Duo Push
We strongly recommend using Duo Push or Web Auth as your second factor, because they’re most secure and can protect against man-in-the-middle (MITM) attacks.
Duo’s flexibility and customizability allows you to find the adaptive authentication method that meets the unique needs of your diverse user base. More

Part VI: Backup and Disaster Recovery – Protecting your network
- Have a formalized, written plan in place
- Prioritize your vulnerable data accordingly
- Stick to your data backup schedules
- Test your backups regularly
- Craft procedures for physical media
- Store your backup data at a secondary location
- Have a Plan
- Backup Offsite
- Develop a Routine
- Test Your Backup
- Have 2 Separate Backups of Your Data
- The BSoD is a full system crash, usually caused by low-level software crashes or faulty hardware.
- Restarting the computer and entering safe mode can help diagnose the problem.
- A minidump file is created when the BSoD occurs, which can be useful for troubleshooting.
- The BSoD information is published in the action center for Windows 7 and newer, allowing for online solutions.
- The BSoD is less common in newer Windows versions, and upgrading can provide better support.
- Direct attached storage connects storage devices directly to a PC or server, but ad-hoc or batch backups lead to out-of-date files.
- Network attached storage connects to the network and offers file server capabilities with redundancy and remote synchronization.
- Disaster protected storage resists disasters that can destroy unprotected data, such as ioSafe’s models.
- Online storage offers cloud-based storage options for businesses or consumers for data backup or incremental backup. The downside is slow data retrieval.
- Private Cloud lets small businesses access privately owned cloud storage using network appliances like Transporter or BitTorrent Sync.
- Offline media, tape drives or optical media like Blu-Ray discs, can still be useful for backup purposes, as demonstrated by Google and Facebook.
- They have high capacity
- Don’t cost much
- Are highly resilient
- Work well if you have massive amounts of information to backup
- They’re additionally secure because they work offline
