
A Modern, Comprehensive Solution Set Designed To Protect Your Business
Cybercriminals are evolving their strategies and attacks every day. You need protection that can keep up. Introducing our Security Stack. Great Lakes Computer has been leading the way by ensuring best-in-class cybersecurity protection is available to all our customers, from SMB to global enterprise. Now, we’ve got a powerhouse of comprehensive services and products that will provide the ultimate level of protection.

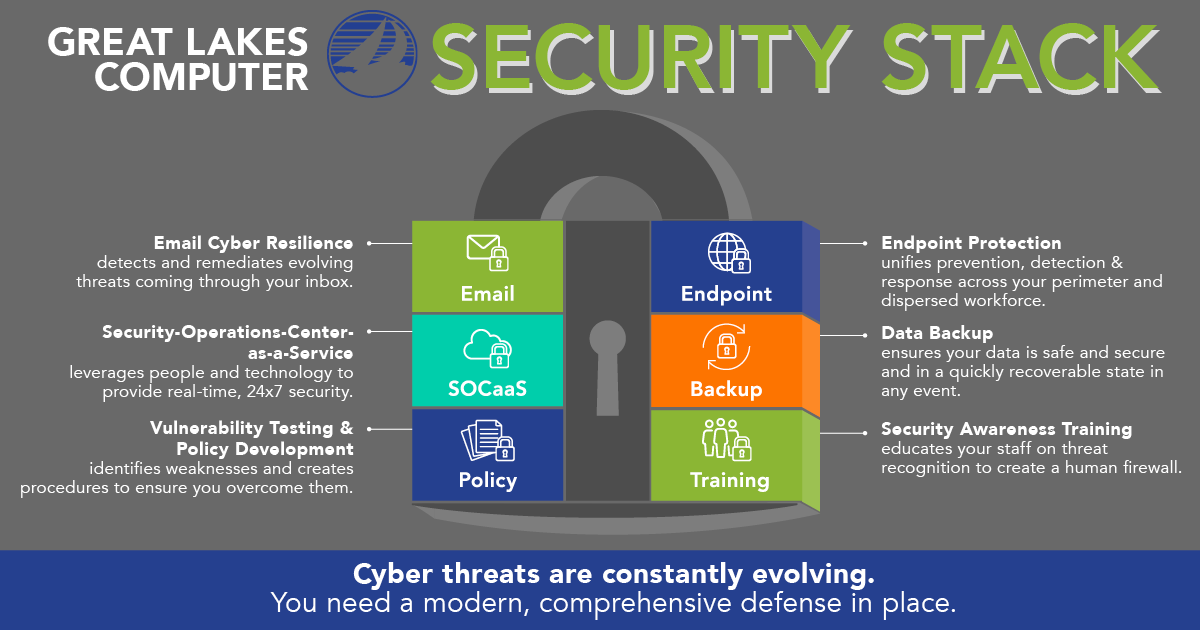
Email Cyber Resilience
Platform
Our cloud-based Secure Email Gateway protects any email platform. It defends against inbound spear-phishing, malware, spam and zero-day attacks by combining innovative applications and policies with multiple detection engines and feeds. Your information is protected by outbound scanning to block threats and prevent loss of sensitive information.
Endpoint Protection
Platform
Our Platform unifies prevention, detection, and response in a single agent powered by machine learning and automation. It provides prevention and detection of attacks across all major vectors, rapid elimination of threats with fully automated, policy-driven response capabilities, and complete visibility into the endpoint environment with full-context, real-time forensics.
Security-Operations-Center-
as-a-Service
Our Managed Security Operations Center combines the power of people, processes, and technology to provide essential security capabilities like real-time threat and intrusion detection, rapid incident response and investigations, and continuous 24/7 monitoring and vulnerability management.
Data Backup
[On-Site & Cloud]
Whether you’re looking for a scalable, on-site backup appliance, direct to cloud or Office 365 spanning, we’ve got you covered. Our solutions offer enterprise level backup and recovery at a price that SMBs can’t afford to pass up. Save time, eliminate human error, and meet regulatory requirements.
3-Step
Human Firewall
Equip your employees with the knowledge and skills they need to protect themselves – and your business – from criminal elements. The most secure companies make their employees the front line of cyber defense. Our 3-step process scans the dark web for your credentials, tests your team with simulated phishing emails, and then trains them on the areas they need it.
Vulnerability Testing
& Policy Development
To be secure, organizations need to regularly test their technical controls, review and update written policies, and ensure their users know how to interact with systems and data safely. We deliver expert knowledge in finding and fixing security problems as well as helping companies meet PCI, SOX, GLBA, HIPAA, and other regulatory requirements.









